12 Best Practices For Cloud Security
Cloud security is a top focus and priority for organizations today. Protecting your organization continues to be increasingly difficult as employees use their own devices and applications for work, and data flows in and out of your business in a variety of ways. On top of that, the COVID-19 pandemic has acted as a major stress test on cybersecurity controls and policies. The resulting surge in remote work brings complexity to the attack surface and brings up many new questions for security teams. While the attack surface has broadened, attacks have also become more sophisticated and more damaging. Today’s security leaders must balance these challenges with business needs to collaborate, innovate, and grow.
Here are the top security best practices you can adopt to secure your cloud solutions:
1. Secrets Management
Many applications require credentials to connect to a database, API keys to invoke a service, or certificates for authentication. Managing and securing access to these secrets could be complicated, and if not properly managed, they can end up in the wrong hands.
Regardless of your solution for managing secrets, here are best practices you should focus on addressing:
Identify all types of passwords, keys and other secrets across your entire IT environment and bring them under centralized management. Continuously discover and onboard new secrets as they are created.
Eliminate hard coded secrets in DevOps tool configurations, build scripts, code files, test builds, production builds, applications, and more. Bring hardcoded credentials under management, such as by using API calls, and enforce password security best practices. Eliminating hardcoded and default passwords effectively removes dangerous backdoors to your environment.
Enforce password security best practices, including password length, complexity, uniqueness expiration, rotation, and more across all types of passwords. Secrets, if possible, should never be shared. If a secret is shared, it should be immediately changed. Secrets to more sensitive tools and systems should have more rigorous security parameters, such as one-time passwords, and rotation after each use.
Apply privileged session monitoring to log, audit, and monitor all privileged sessions (for accounts, users, scripts, automation tools, etc.) to improve oversight and accountability. This can also entail capturing keystrokes and screens (allowing for live view and playback). Some enterprise privilege session management solutions also enable IT teams to pinpoint suspicious session activity in-progress, and pause, lock, or terminate the session until the activity can be adequately evaluated.
Extend secrets management to third-parties — ensure partners and vendors conform to best practices in using and managing secrets.
Threat analytics — continuously analyze secrets usage to detect anomalies and potential threats. The more integrated and centralized your secrets management, the better you will be able to report on accounts, keys applications, containers, and systems exposed to risk.
DevSecOps — With the speed and scale of DevOps, it’s crucial to build security into both the culture and the DevOps lifecycle (from inception, design, build, test, release, support, maintenance). Embracing a DevSecOps culture means that everyone shares responsibility for security, helping ensure accountability and alignment across teams. In practice, this should entail ensuring secrets management best practices are in place and that code does not contain embedded passwords in it.
2. Web Application Firewall (WAF)
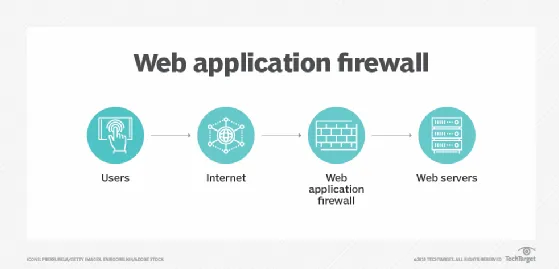
Web application firewall (WAF) provides centralized protection of your web applications from common exploits and vulnerabilities. WAF helps protect your web applications and APIs against common web exploits that may affect availability, compromise security, or consume excessive resources. WAF gives you control over how traffic reaches your applications by enabling you to create security rules that block common attack patterns, such as SQL injection or cross-site scripting, and rules that filter out specific traffic patterns you define.
3. Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an extra layer of protection on top of your user name and password. With MFA enabled, when a user signs in, they will be prompted for their username and password (the first factor — what they know), as well as for an authentication code from their MFA device (the second factor — what they have). Taken together, these multiple factors provide increased security for your Cloud account settings and resources.
Enforce multi-factor authentication for users, especially administrators and others in your organization who can have a significant impact if their account is compromised.
4. Encrypt Virtual Hard Disk Files
Encrypt your virtual hard disk files to help protect your boot volume and data volumes at rest in storage, along with your encryption keys and secrets. Disk Encryption helps you encrypt your Windows and Linux IaaS virtual machine disks.
The following are the best practices for using Disk Encryption:
Enable encryption on VMs.
Use a key encryption key (KEK) for an additional layer of security.
Take a snapshot and/or backup before disks are encrypted. Backups provide a recovery option if an unexpected failure happens during encryption.
5. Use Strong Network Controls
You can connect virtual machines (VMs) and appliances to other networked devices by placing them on virtual networks. That is, you can connect virtual network interface cards to a virtual network to allow TCP/IP-based communications between network-enabled devices. Virtual machines connected to a virtual network can connect to devices on the same virtual network, different virtual networks, the internet, or your own on-premises networks.
As you plan your network and the security of your network, centralize:
Management of core network functions like virtual network and subnet provisioning, and IP addressing.
Governance of network security elements, such as network virtual appliance functions like virtual network and subnet provisioning, and IP addressing. If you use a common set of management tools to monitor your network and the security of your network, you get clear visibility into both. A straightforward, unified security strategy reduces errors because it increases human understanding and the reliability of automation.
Best practices for logically segmenting subnets include:
Don’t assign Allow rules with broad ranges (e.g. allow 0.0.0.0 through 255.255.255.255).
Segment the larger address space into subnets.
Create network access controls between subnets. Routing between subnets happens automatically, and you don’t need to manually configure routing tables. By default, there are no network access controls between the subnets that you create on a virtual network.
Avoid small virtual networks and subnets to ensure simplicity and flexibility.
6. Mitigate And Protect Against DDoS
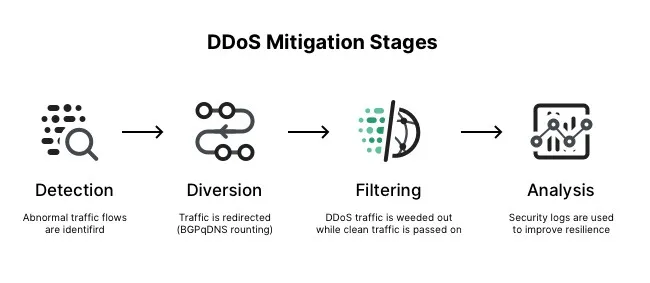
Distributed denial of service (DDoS) is a type of attack that tries to exhaust application resources. The goal is to affect the application’s availability and its ability to handle legitimate requests. These attacks are becoming more sophisticated and larger in size and impact. They can be targeted at any endpoint that is publicly reachable through the internet. Designing and building for DDoS resiliency requires planning and designing for a variety of failure modes.
Following are the best practices for building DDoS-resilient services:
Ensure that security is a priority throughout the entire lifecycle of an application, from design and implementation to deployment and operations. Applications can have bugs that allow a relatively low volume of requests to use a lot of resources, resulting in a service outage.
Design your applications to scale horizontally to meet the demand of an amplified load, specifically in the event of a DDoS attack. If your application depends on a single instance of a service, it creates a single point of failure. Provisioning multiple instances makes your system more resilient and more scalable.
Layering security defenses in an application reduces the chance of a successful attack. Implement secure designs for your applications by using the built-in capabilities of the Cloud provider.
7. Manage Your VM Updates
Cloud VMs, like all on-premises VMs, are meant to be user managed. The cloud provider doesn’t push Windows or Linux updates to them. You need to manage your VM updates.
Here are the best practices to manage your VM updates:
Keep your VMs current. Use the update management solution by your cloud provider.
Ensure at deployment that images you built include the most recent round of Windows or Linux updates.
Periodically redeploy your VMs to force a fresh version of the OS.
Rapidly apply security updates to VMs.
Deploy and test a backup solution.
8. Enable Password Management
If you have multiple tenants or you want to enable users to reset their own passwords, it’s important that you use appropriate security policies to prevent abuse.
Here are the best practices to manage your passwords:
Set up self-service password reset (SSPR) for your users
Monitor how or if SSPR is really being used.
Extend cloud-based password policies to your on-premises infrastructure.
9. Role-Based Access Control (RBAC)
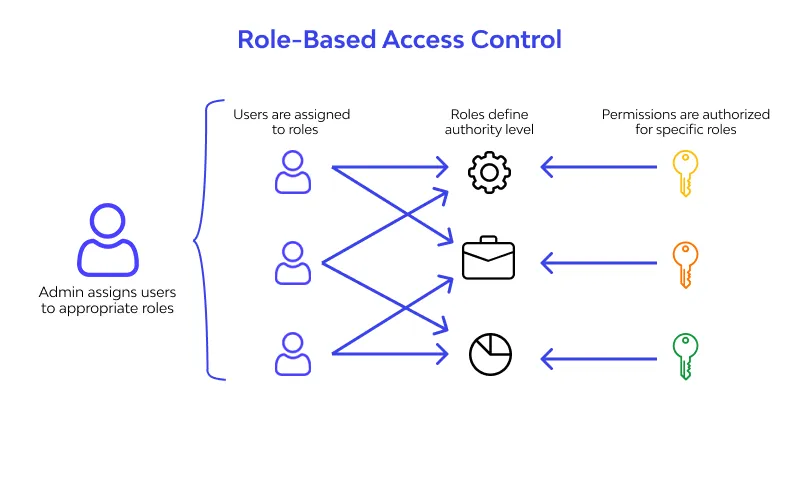
Using role-based access control (RBAC) for cloud resources is critical for any organization that uses the cloud. Role-based access control helps you manage who has access to cloud resources, what they can do with those resources, and what areas they have access to. Designating groups or individual roles responsible for specific functions in the cloud helps avoid confusion that can lead to human and automation errors that create security risks. Restricting access based on the need to know and least privilege security principles is imperative for organizations that want to enforce security policies for data access. Your security team needs visibility into your cloud resources in order to assess and remediate risk. If the security team has operational responsibilities, they need additional permissions to do their jobs. You can use RBAC to assign permissions to users, groups, and applications at a certain scope. The scope of a role assignment can be a subscription, a resource group, or a single resource.
Best practices for using RBAC to manage access to your cloud resources are:
Segregate duties within your team and grant only the amount of access to users that they need to perform their jobs. Instead of giving everybody unrestricted permissions in your cloud subscription or resources, allow only certain actions at a particular scope.
Grant security teams with responsibilities access to see cloud resources so they can assess and remediate risk.
Grant the appropriate permissions to security teams that have direct operational responsibilities.
Organizations that don’t enforce data access control by using capabilities like RBAC might be giving more privileges than necessary to their users. This can lead to data compromise by allowing users to access types of data (e.g. high business impact) that they shouldn’t have.
10. Perform Security Penetration Testing
Validating security defenses is as important as testing any other functionality. Make penetration testing a standard part of your build and deployment process. Schedule regular security tests and vulnerability scanning on deployed applications, and monitor for open ports, endpoints, and attacks.
Fuzz testing is a method for finding program failures (code errors) by supplying malformed input data to program interfaces (entry points) that parse and consume this data. Use tools from your cloud provider to look for bugs and other security vulnerabilities in your software before you deploy it to cloud. It will help you catch vulnerabilities before you deploy software so you don’t have to patch a bug, deal with crashes, or respond to an attack after the software is released.
11. Keep Up To Date With Security Recommendations
Stay up to date with the security recommendations by your cloud provider to evolve the security posture of your workload. Cloud provider services like Azure Security Center, AWS Security Hub and Google Cloud Security Command Center periodically analyze the security state of your cloud resources to identify potential security vulnerabilities. It then provides you with recommendations on how to remediate those vulnerabilities.
12. Build An Incident Response Plan
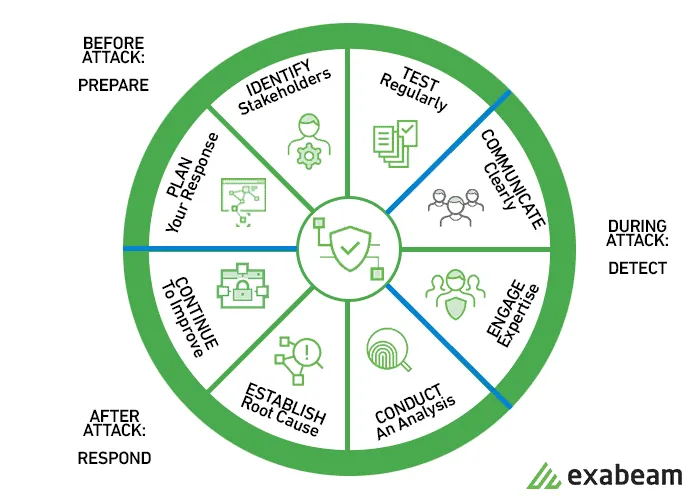
Preparation is critical to timely and effective investigation, response to, and recovery from security incidents to help minimize disruption to your organization.
Best Practices:
Identify key personnel and external resources: Identify internal and external personnel, resources, and legal obligations that would help your organization respond to an incident.
Develop incident management plans: Create plans to help you respond to, communicate during, and recover from an incident. For example, you can start an incident response plan with the most likely scenarios for your workload and organization. Include how you would communicate and escalate both internally and externally.
Prepare forensic capabilities: Identify and prepare forensic investigation capabilities that are suitable, including external specialists, tools, and automation.
Automate containment capability: Automate containment and recovery of an incident to reduce response times and organizational impact.
Pre-provision access: Ensure that incident responders have the correct access pre-provisioned to reduce the time for investigation through to recovery.
Pre-deploy tools: Ensure that security personnel have the right tools pre-deployed to reduce the time for investigation through to recovery.
Run game days: Practice incident response game days (simulations) regularly, incorporate lessons learned into your incident management plans, and continuously improve.
Conclusion
It is clear that although the use of cloud computing has rapidly increased, security is still a major concern in the cloud computing environment.
Cloud security is not just a technical problem. It also involves standardization, monitoring, policies, and many other aspects.